What is Phishing & How to Avoid Becoming a Victim
October is Cybersecurity month. This month we will be featuring a series of blogs for your education of the on-line dangers and how to make safe choices.
One of the most common ways to become entangled a breach is by being a phishing victim.
Here are a few facts to consider:
2 Million: Phishing attacks were reported in 2016 — a 65% increase from 2015 *
46% of US survey respondents have fallen victim to a phishing scam **
30% of working adults do not understand what phishing is ***
15% of phishing victims will click a dangerous attachment again**
So, what exactly is Phishing?
Phishing is when cybercriminals send malicious emails designed to trick people into falling for a scam. Phishing is an example of social engineering: a collection of techniques, including forgery, misdirection, and lying by which scam artists manipulate human psychology.
The intent of these techniques is to get users to reveal personal and financial information, system credentials, or other sensitive data - like financial account data, credit card numbers, and tax and medical records — as well as private business data, like customer names and contact information, proprietary product secrets, and confidential communications.
Cybercriminals also use phishing attacks to gain direct access to email, social media, and other accounts — or to obtain permissions to modify and compromise connected systems, like point of sale terminals and order processing systems. Three primary mechanisms within phishing emails are used to steal your information: malicious web links, malicious attachments, and fraudulent data-entry forms.
Those who fall for phishing scams may end up with malware infections (including ransomware), identity theft, and data loss. Examples of the consequences of falling for a phishing attack, either at home or at work are:
In Your Personal Life
- Money stolen from your bank account
- Fraudulent charges on credit cards
- Tax returns filed in your name
- Loans and mortgages opened in your name
- Lost access to photos, videos, files, etc.
- Fake social media posts made in your accounts
At Work
- Loss of corporate funds
- Exposed personal information of customers and coworkers
- Outsiders access to confidential communications, files, and systems
- Files become locked and inaccessible
- Damage to employer's reputation
Should you be presented with a suspicious email, reference the decision tree infographic by Wombat Security for a quick guide on how to make smart choices.
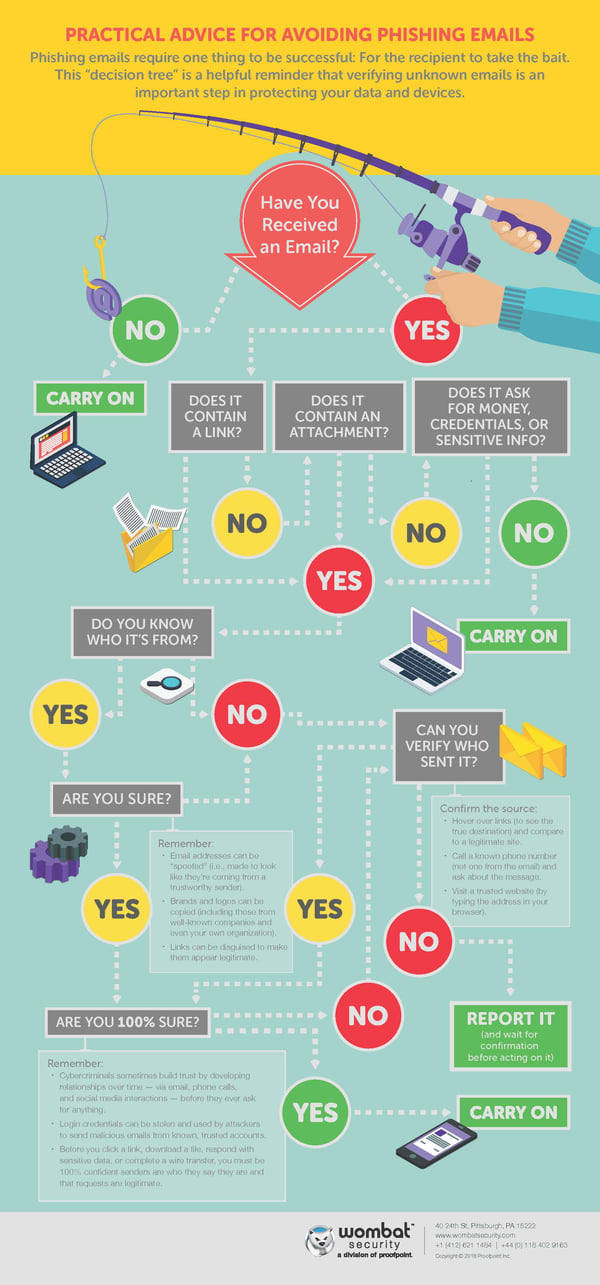
Take time to share this information with friends and colleagues. Be a proactive participant in this month’s Cybersecurity awareness efforts.
To best review ways to protect you and your business’s information, confer with an expert. An agnostic technology agent or consultant can ask the right questions to determine what you need, help you gain a deeper overview of the wide range of solutions available and how each one fits in with what you’re trying to accomplish. In addition to assisting you with procurement, they can also handle ongoing care.
*(Source: The Anti-Phishing Working Group)
**(Source: Verizon’s 2017 Data Breach Investigations Report)
*** (Source: Wombat Security’s 2017 User Risk Report)
About Simplicity
Simplicity VoIP, based in Richmond, VA, provides hosted PBX, VoIP and business telephone solutions nationally to small, medium, and enterprise-level businesses for a comprehensive unified communications experience. Two distinct Class 5 geo-redundant VoIP platforms are offered in addition to fax-to-email, phones and equipment, and managed services. Named as Richmond’s 11th fastest growing company by Richmond BizSense, Simplicity VoIP’s key to success is its on-site service, installation and training supported 24/7/365 by a world-class client services team.




