What is Ransomware & How to Avoid Becoming a Victim
October is Cybersecurity month. This month we will be featuring a series of blogs for your education of the on-line dangers and how to make safe choices.
One of the most frightening attacks today is RANSOMWARE.
What is ransomware?
Ransomware is malicious software (malware) that cybercriminals can use to either block or threaten to publish a victim’s data unless a sum of money or ransom is paid. Cybercriminals will attack any consumer or any business from all industries. Ransomware started as a concept in 1996 but has begun to become more popular with the growth of cyptocurrencies, such as Bitcoin.
Here are a few facts to consider:
- 4,000: An average of ransomware episodes occurring every day.*
- 49%: Ransomware is the top variety of malicious software and is found in 39% of cases where malware was identified.**
- 46% of respondents could correctly define ransomware.***
- 42% of respondents could not correctly identify ransomware****
- $301,000,000 - ransoms paid by small to medium-sized businesses between Q2 2016 and Q2 2017*****
How does ransomware work?
- Ransomware attacks typically start with an email that includes a link or attachment that looks legitimate
- When the user clicks on ransomware link or attachment, the malware with anti-sandboxing techniques is enabled
- A ransomware message is deployed from other infected computers
- A ransomware payment screen appears
Types of Ransomware
Ransomware takes many forms, but the most common types are as follows:
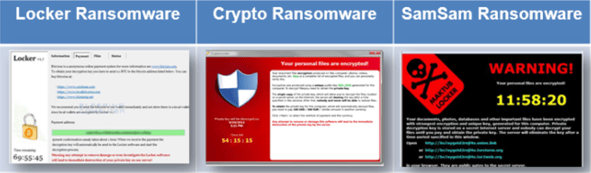
| Endpoint | Requires End User | Requires End User | Remote Execution |
| Delivery Method | Social Engineering | Favors TOR | Vulnerable Servers |
| Impact on Data | Locks System | Encrypts Files | Encrypts Files |
| Payment | Bitcoin Payment | Bitcoin Payment | Bitcoin payment |
Ransomware Response
Develop an Incident Response Plan. If ransomware strikes, a fast response time is crucial to having any chance of recovering data. Immediately disconnect your device from all available networks it is connected to, turn off any wireless capabilities, and unplug any external hard drives or USBs. Then do an assessment of the scope and strain of the attack can begin in order to determine a response.
Should you pay up?
Several government agencies, including the FBI, advise against paying the ransom.
Consider this:
- There is no guarantee that you will get your data back – depending on the malware, victim’s files are actually destroyed.
- The goal of the attacker is to receive payment, which may or may not remove the ransomware.
- Payment encourages the ransomware cycle.
- Half of victims who pay the ransom are likely to suffer from repeat attacks.
What should you do? Instead of paying the ransom, it is recommended to restore the lost data via backups.
Ransomware Prevention
Practice prevention, not remediation. It’s easier to avoid ransomware attacks altogether than it is to remove ransomware.
- User education is one of the most powerful weapons in the fight against ransomware — especially as ransomware continues to evolve. Good anti-phishing behaviors are, by extension, the best ransomware prevention money can buy.
- Conduct regular back-ups and monitor back-up systems
- Deploy frequently updated anti-virus and content filtering rules
- Perform regular perimeter vulnerability scans and pen tests
For more information about ransomware, reference the infographic by Wombat Security.
Take time to share this information with friends and colleagues. Be a proactive participant in this month’s Cybersecurity awareness efforts.
To best review ways to protect you and your business’s information, confer with an expert. An agnostic technology agent or consultant can ask the right questions to determine what you need, help you gain a deeper overview of the wide range of solutions available and how each one fits in with what you’re trying to accomplish. In addition to assisting you with procurement, they can also handle ongoing care.
About Simplicity
Simplicity VoIP, based in Richmond, VA, provides hosted PBX, VoIP and business telephone solutions nationally to small, medium, and enterprise-level businesses for a comprehensive unified communications experience. Two distinct Class 5 geo-redundant VoIP platforms are offered in addition to fax-to-email, phones and equipment, and managed services. Named as Richmond’s 11th fastest growing company by Richmond BizSense, Simplicity VoIP’s key to success is its on-site service, installation and training supported 24/7/365 by a world-class client services team.
*(Source: FBI Internet Crime Report)
**(Source: Verizon’s 2017 Data Breach Investigations Report)
*** (Source: State of Phishing Report
****Wombat Security’s 2017 User Risk Report)
***** State of the Channel Ransomware Report





